Intro
Boost business success with 5 NIST tips, enhancing cybersecurity, risk management, and compliance, while improving data protection and privacy practices.
The importance of cybersecurity in today's business world cannot be overstated. With the increasing number of cyber threats and attacks, it's essential for businesses to take proactive measures to protect themselves. The National Institute of Standards and Technology (NIST) provides a framework for businesses to follow to improve their cybersecurity posture. In this article, we'll explore five NIST business tips that can help your organization stay safe from cyber threats.
Implementing a robust cybersecurity framework is crucial for businesses of all sizes. Cyber attacks can result in significant financial losses, damage to reputation, and loss of customer trust. By following the NIST framework, businesses can reduce the risk of cyber attacks and ensure the confidentiality, integrity, and availability of their data. Whether you're a small startup or a large enterprise, these five NIST business tips can help you improve your cybersecurity and stay ahead of the threats.
The NIST framework is based on five core functions: Identify, Protect, Detect, Respond, and Recover. These functions provide a structured approach to managing cybersecurity risk and can be applied to businesses of all sizes. By understanding and implementing these functions, businesses can improve their cybersecurity posture and reduce the risk of cyber attacks. In the following sections, we'll delve deeper into each of these functions and provide practical tips for implementation.
Understanding the NIST Framework
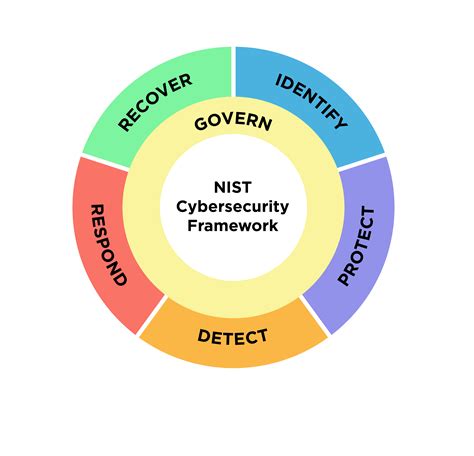
Benefits of the NIST Framework
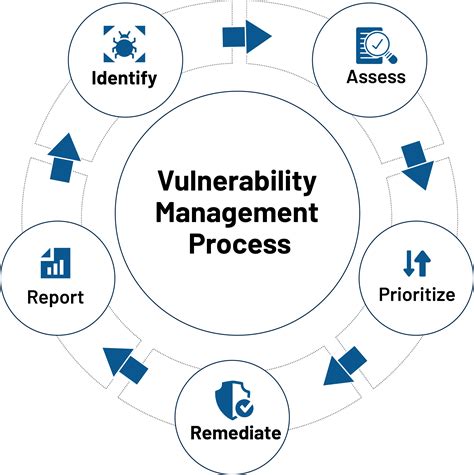
The benefits of the NIST framework are numerous. It provides a structured approach to managing cybersecurity risk, which can help businesses reduce the risk of cyber attacks. The framework is also flexible and adaptable, making it suitable for businesses of all sizes. Additionally, the NIST framework provides a common language and set of standards for cybersecurity, which can help businesses communicate more effectively with their stakeholders.Tip 1: Identify Your Assets

Some of the key assets that you should identify include:
- Customer data
- Financial information
- Intellectual property
- Network infrastructure
- Cloud services
Conducting an Asset Inventory
Conducting an asset inventory is an essential step in identifying your assets. This involves creating a list of all of the assets that are critical to your business operations. You should include both physical and digital assets, such as laptops, smartphones, and cloud services. By conducting an asset inventory, you can determine which assets are most critical and require the most protection.Tip 2: Protect Your Assets

Implementing Security Controls
Implementing security controls is essential to protecting your assets. This involves configuring your security controls to prevent unauthorized access or malicious activity. You should also regularly review and update your security controls to ensure that they are effective and up-to-date.Tip 3: Detect and Respond to Threats
Developing an Incident Response Plan
Developing an incident response plan is essential to detecting and responding to threats. This involves creating a plan that outlines the steps that you will take in response to a cyber attack. Your incident response plan should include procedures for containment, eradication, recovery, and post-incident activities.Tip 4: Recover from Incidents

Conducting Post-Incident Activities
Conducting post-incident activities is essential to recovering from incidents. This involves reviewing the incident to determine what happened and how to prevent it from happening again. You should also conduct a lessons learned exercise to identify areas for improvement and implement changes to your security controls.Tip 5: Continuously Monitor and Improve
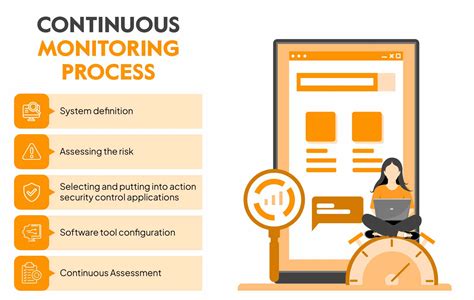
Conducting Regular Risk Assessments
Conducting regular risk assessments is essential to continuously monitoring and improving your cybersecurity posture. This involves identifying, assessing, and prioritizing risks to your assets. You should also implement risk mitigation strategies to reduce the risk of cyber attacks.Nist Business Tips Image Gallery








What is the NIST framework?
+The NIST framework is a widely adopted standard for managing cybersecurity risk. It provides a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats.
Why is cybersecurity important for businesses?
+Cybersecurity is important for businesses because it helps protect against cyber attacks, which can result in significant financial losses, damage to reputation, and loss of customer trust.
How can businesses implement the NIST framework?
+Businesses can implement the NIST framework by following the five core functions: Identify, Protect, Detect, Respond, and Recover. This involves identifying assets, implementing security controls, detecting and responding to threats, recovering from incidents, and continuously monitoring and improving cybersecurity posture.
What are some common cybersecurity threats that businesses face?
+Some common cybersecurity threats that businesses face include phishing, ransomware, malware, and denial-of-service attacks. Businesses should also be aware of insider threats, such as employees intentionally or unintentionally compromising security.
How can businesses stay up-to-date with the latest cybersecurity threats and trends?
+Businesses can stay up-to-date with the latest cybersecurity threats and trends by regularly reviewing cybersecurity news and updates, attending industry conferences, and participating in cybersecurity training and awareness programs.
We hope that this article has provided you with a comprehensive understanding of the NIST framework and how to implement it in your business. By following the five core functions and tips outlined in this article, you can improve your cybersecurity posture and reduce the risk of cyber attacks. Remember to continuously monitor and improve your cybersecurity posture to stay ahead of the threats. If you have any questions or comments, please don't hesitate to reach out. Share this article with your colleagues and friends to help spread awareness about the importance of cybersecurity. Together, we can create a safer and more secure digital world.
