Intro
Boost security with 5 HM-232 tips, featuring encryption, access control, and threat prevention strategies to protect against cyber attacks and data breaches.
The importance of security in today's world cannot be overstated. With the rise of technology and the internet, security threats have become more sophisticated and widespread. It is essential for individuals and organizations to take proactive measures to protect themselves from these threats. In this article, we will discuss 5 HM-232 security tips that can help you enhance your security posture.
Security is a critical aspect of our lives, and it is essential to take it seriously. From protecting our personal identities to safeguarding our businesses, security is a top priority. The HM-232 security protocol is a widely used standard for securing sensitive information, and it provides a framework for implementing robust security measures. By following these 5 HM-232 security tips, you can significantly reduce the risk of security breaches and protect your assets.
The world of security is constantly evolving, with new threats emerging every day. It is crucial to stay ahead of these threats by implementing the latest security protocols and best practices. The HM-232 security protocol is a widely recognized standard that provides a comprehensive framework for securing sensitive information. By following these 5 HM-232 security tips, you can ensure that your security measures are aligned with industry best practices and that you are well-equipped to handle emerging threats.
Understanding HM-232 Security Protocol

Key Components of HM-232 Security Protocol
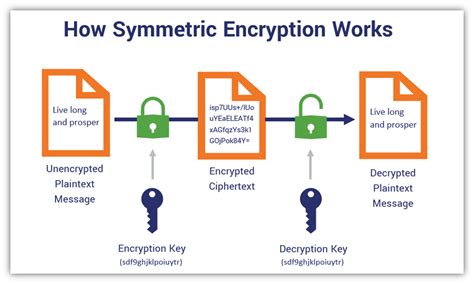
The HM-232 security protocol consists of several key components, including: * Data encryption: This involves encrypting sensitive data to prevent unauthorized access. * Secure authentication: This involves verifying the identity of users and devices to prevent unauthorized access. * Access control: This involves controlling access to sensitive information based on user roles and permissions. By understanding these key components, you can implement the HM-232 security protocol effectively and ensure that your security measures are robust and effective.Implementing HM-232 Security Tips

Benefits of Implementing HM-232 Security Tips
Implementing the HM-232 security protocol can provide several benefits, including: * **Improved security posture**: Implementing the HM-232 security protocol can significantly improve your security posture and reduce the risk of security breaches. * **Compliance with regulations**: The HM-232 security protocol is widely recognized and accepted, and implementing it can help you comply with regulatory requirements. * **Protection of sensitive information**: The HM-232 security protocol provides a comprehensive framework for protecting sensitive information, including personal identifiable information (PII) and sensitive business data. By implementing the HM-232 security protocol, you can ensure that your security measures are robust and effective and that you are well-equipped to handle emerging threats.Best Practices for HM-232 Security

Common Mistakes to Avoid
When implementing the HM-232 security protocol, there are several common mistakes to avoid, including: * **Using weak encryption**: Using weak encryption algorithms can compromise the security of sensitive data. * **Failing to implement secure authentication**: Failing to implement secure authentication can allow unauthorized access to sensitive information. * **Failing to monitor and audit**: Failing to monitor and audit security events can make it difficult to detect and respond to security incidents. By avoiding these common mistakes, you can ensure that your security measures are robust and effective and that you are well-equipped to handle emerging threats.Conclusion and Next Steps

Final Thoughts
Security is a critical aspect of our lives, and it is essential to take it seriously. By implementing the HM-232 security protocol and following best practices, you can ensure that your security measures are robust and effective. Stay vigilant, stay informed, and stay ahead of emerging threats.HM-232 Security Image Gallery







What is the HM-232 security protocol?
+The HM-232 security protocol is a widely recognized standard for securing sensitive information. It provides a comprehensive framework for implementing robust security measures, including encryption, access control, and authentication.
How do I implement the HM-232 security protocol?
+To implement the HM-232 security protocol, you should start by conducting a thorough risk assessment to identify vulnerabilities and weaknesses in your security measures. Then, implement the 5 HM-232 security tips outlined in this article, including using strong encryption, implementing secure authentication, controlling access, monitoring and auditing, and training personnel.
What are the benefits of implementing the HM-232 security protocol?
+Implementing the HM-232 security protocol can provide several benefits, including improved security posture, compliance with regulatory requirements, and protection of sensitive information. By implementing the HM-232 security protocol, you can significantly reduce the risk of security breaches and ensure that your security measures are robust and effective.
How often should I conduct security audits?
+Security audits should be conducted regularly to identify vulnerabilities and weaknesses in your security measures. The frequency of security audits will depend on your organization's specific needs and risk profile. However, it is recommended to conduct security audits at least annually, or more frequently if you are in a high-risk industry or have experienced a security breach.
What is the importance of security awareness training?
+Security awareness training is critical to ensuring that personnel understand security best practices and can respond to security incidents effectively. Security awareness training should be provided regularly to all personnel, and should cover topics such as password management, phishing, and incident response.
We hope that this article has provided you with valuable insights and information on the HM-232 security protocol. By implementing the 5 HM-232 security tips outlined in this article, you can significantly improve your security posture and reduce the risk of security breaches. Remember to stay vigilant, stay informed, and stay ahead of emerging threats. If you have any questions or comments, please feel free to share them with us. We would love to hear from you and provide you with any additional information or guidance you may need.
